18 September 2025
Webinar: How hackers steal your passwords in 2025 and how to stop them
With the exponential growth of cyber attacks and methods over the last two years, the increasing threat of AI based security attacks, and even sophisticated phishing attacks that can evade detection, and even bypass multi-factor authentication, iBizify is continually investigating and deploying new methods and services to secure its managed IT clients safe.
A key area of security for all businesses is passwords and the methods you use to log into applications. Whether you require a second device, one-time password, verification code or some other form of additional step to log in, all of them leave gaps for hackers to take advantage of.
iBizify’s trusted security partner Brigantia are offering a free webinar that will cover everything you need to know about the problem with traditional password processes. Join to discover …
- Why your login credentials aren't as safe as you think (even with MFA enabled!)
- How hackers are stealing passwords
- The impact of weak password security
The webinar will take place on:
Thursday 9th October, at 11am (GMT)
We look forward to you joining the session.
To reserve your spot on the webinar, follow this link:
https://us06web.zoom.us/webinar/register/3917582061193/WN_qDG0iNsBQROMaJji069VHw
13 June 2025
Sophisticated new phishing attacks
Most people are aware of the risk of clicking malicious links. However, iBizify would like to highlight a relatively new, growing security threat. The attack is sophisticated, executed by coordinated human teams, assisted by AI. It can bypass standard security mechanisms, and is performed discreetly.
It targets users of Microsoft 365 Business services, and other similar services. This phishing attack is particularly concerning, given that it uses sophisticated methods to effectively bypass multi-factor authentication – which is a common first line of defence against phishing attacks and password compromises.
⚠️ These emails will usually come from someone you know. The email address will be true and correct. It may pass standard security checks.
The cause
The breach begins with a phishing email or message that comes from a familiar address, such as a colleague, friend, or family. They may include the sender’s legitimate email signature, their name, and other details, making them look extremely convincing.
Here are a couple of examples of such email content, but the email may take any form:
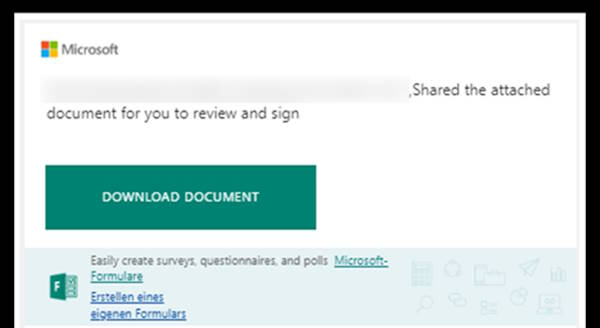
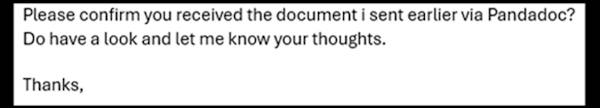
These attacks often evade the detection of standard security software, due to the verified sender, and the use of an “innocent” service, such as OneNote, Pandadoc, amongst others.
The effect
The following describes the general nature of attacks iBizify has evaluated. In fact, every attack and its process can be very different.
Exercise extreme caution if you receive an email asking you to open a document or click a link, even if you know the sender. These links may lead to phishing sites that collect your login details and register a new multifactor authentication device for further access. Attackers could gain full remote access to your mailbox and other services.
Unlike regular attacks in the past, these are often handled in by human teams, who are on standby to maximise the attack in real time.
Typically, the attacker downloads copies of all accessible information. Within the mailbox, mail rules are configured to conceal activities, followed by the dispatch of hundreds or thousands of phishing emails to contacts. Sent items are automatically deleted, and incoming emails are also removed to hide concerned replies. An automatic response is sent to further convince recipients of the legitimacy of the phishing email.
After a breach, attackers often analyse stolen data to understand the victim’s systems and maximise their gains, delaying the actual attack by days or weeks. This delay increases the impact, as victims may be unaware of the breach for some time, making the original cause harder to identify.
When your email account is compromised in this way, attackers typically collect addresses from all your past emails, not just your contacts in the address book. The impact is thus far greater than similar attacks in the past.
If an email link or request for action is unexpected, don't click or respond - even if you know the sender. If you're unsure why you received the document, verify by phoning the sender first.
⚠️ Never use email to question the validity of an email you have received. If the sender’s account has been compromised, the response may well come from the attack team!

What to do about it
If you believe you may have clicked through and shared your details, please contact iBizify or your trusted IT service / support provider for urgent advice. I urge you to remain vigilant and take precautions to protect your accounts and information.
To help prevent such breaches, and be better prepared should you experience one:
- Always exercise caution and maintain vigilance. Consider implementing continuous awareness training such as KnowBe4 to ensure that you and your colleagues remain alert and aware of potential threats.
- Use strong unique passwords, and multifactor authentication. Use a business-grade password management solution such as Keeper Security to securely store passwords and other sensitive information.
- Review if it is possible to prevent phishing attacks altogether by deploying a phish-proof, password-free solution such as AuthN by IDEE.
- Use a secure, encrypted backup and security service such as Sentinel that stores data separately from your main systems. Include both cloud-based data and critical devices.
- Use managed IT services. The IT landscape is constantly evolving, so ensure your service is properly set up, administered and maintained by a reliable and knowledgeable service provider. Manage365 provides such a service for Microsoft 365 users.
- Deploy a managed security solution such as iBizify's Secure365 for Microsoft 365 users: Installing anti-virus and a few software packages is insufficient. A suitable combination of tools, front line and fallback security layers, along with managed monitoring, alerts, and reporting, introduces a critical human element to this ongoing challenge.
- Auditing: Make sure you have a full record of who and what is being accessed and why.
- Conditional access: define who, how, why and when anyone can access your system – whether they have a password or not.
- Always keep your online service configurations, computers, devices and security baselines up to date to minimise vulnerabilities.
- Do not allow your staff to use insecure, unpatched or outdated devices to connect to your IT services. iBizify's Sentinel offers endpoint security, backup, identifies and patches vulnerabilities.
Need help? iBizify has supported many business and personal clients, including IT companies and service providers, in handling and preventing attacks and breaches. We have assisted with email, website, phone, and other online service attacks.
31 October 2024
Don’t get phished!
Malicious messages are on the rise. Industry experts estimate that such attacks have risen over 6- to 10-fold since the beginning of the COVID19 pandemic in 2020. In iBizify’s opinion, these threats are now the most significant, beyond traditional malware and direct attacks.
Whilst most attacks are delivered by email, such messages can be delivered via almost any medium including email, text, social media, WhatsApp and even phone calls.

These threats deceive people into revealing sensitive information such as passwords, bank account details, etc. and can be categorised into two variations:
- Phishing: Generalised attacks that are usually sent en masse. The purpose being to catch victims by targeting large numbers within each campaign.
- Spear Phishing: These are highly curated and sophisticated. They usually include more specific information about the targeted individual, such as mentioning several names of people known to the individual, specifying their company name, bank information or specific online services they are known to use.
Seemingly benign phishing attacks are often used to gather intelligence to prepare a Spear Phishing attack.
How do I spot a Phishing email?
THINK BEFORE YOU CLICK! Look out for…
- Urgent, Important, Overdue, flagged as important
- Requests for personal information
- File attachments that lead to very genuine-looking login pages
- Invoices, voicemails or messages waiting for you
- Missed deliveries, parcel tracking
- Your account or password has expired or blocked
- Your computer or account is infected
- Social cues "saw you in this video", "did you really do this?!", etc.
- Claims to be from Apple / Microsoft / Google / Amazon tech support
If you are still convinced the message is genuine, and feel the need to click:
Hover over links to reveal the actual destination. Look at the domain name – the bit before the .com, .co.uk, etc. If the email claims to be from Lloyds Bank, but the destination domain is not a Lloyds domain but rather amazonaws.com (a commonly used tool for phishing) or some other unknown value, then do not click!
Consider not using the email links at all, and instead contact the provider directly using known-good contact information.
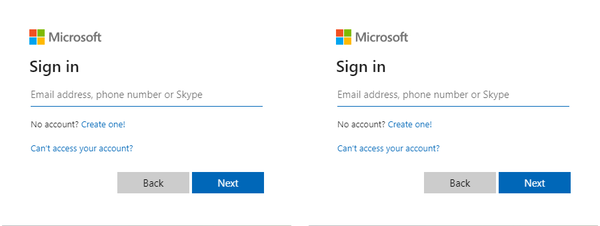
Can you spot the difference between this genuine sign-in page and the fake one?
Be aware
Malicious messages may appear to be from someone you know, they may even include your friend or colleague’s name and contact details. Never assume a message is safe even if it is from a known contact.
You will never get legitimate messages direct from Microsoft / Apple support claiming they have detected malware on your device (or similar).
Never let anyone connect to your device unless you truly know who they are, and have especially good reason to do so.
Be secure
- Maintain your software and devices with the latest updates. Install them promptly and frequently. Don’t forget your PCs, Macs, Android, iPhone, iPads
- USE MULTIFACTOR AUTHENTICATION on any online accounts that you can.
For example, if you use Microsoft online services, set up “Microsoft Authenticator” on your phone. Doing so will help to protect your account even if your password is compromised - ALWAYS use complex passwords for all your online services
- NEVER re-use passwords on multiple online accounts
If you do, if one is compromised, its details will be stored on a database and then used to successfully attack your other accounts (this happens more than you think!) - AVOID using your business email address to sign up for circulars/newsletters or other bulk mail. Doing so shares your email address more widely and makes it harder to filter genuine email. If you want these messages, consider instead setting up a free personal email address to receive them.
- Discuss with your IT provider about how to filter and minimise these attacks
Use password management
Here is an example of a strong password:
8Q{{a>0g13C9gi29.<yW
Could you remember this and type it in every time? Probably not, which is a solid reason to make use of a reputable password manager such as Keeper Security.
Report attacks
For the collective sake of your organisation and others, always report malicious emails if you can. Doing so will help prevent others from receiving the same.
- Check with your organisation’s IT administration or support to see if they have a reporting mechanism.
- Common email tools such as Outlook have dedicated report buttons that you can use. Simply select the message and click the Report Message button.
- If you don’t have these options, consider forwarding the message to report@phishing.gov.uk for the National Cyber Security Centre (NCSC) to review.
Caught out?
If you believe you may have shared your login details or other sensitive information, please change any relevant passwords and contact the host of the service for advice. If you are part of an organisation, then inform your manager. If you shared financial information, contact your bank or card provider as soon as possible. For more information on what to do please visit https://www.ncsc.gov.uk/collection/phishing-scams/what-to-do.
Need help?
If your organisation is an iBizify Manage subscriber, we will already be supporting you in securing your systems and helping your staff to work safely.
iBizify offers a wide range of managed security tools and services from backups, and password managers to vulnerability and endpoint assessments, and online security baselining.
If you have any questions or would like to discuss your IT security, then contact us by scheduling a call at https://ibizify.net/callback/
22 August 2023
How to set up Microsoft Authenticator
These instructions assume you already have a Microsoft 365 account set up with a username and password. They are aimed at iBizify Microsoft 365 customers.
- Sign in to your Microsoft 365 account at office.com.
- Click your profile icon in the top-right, then View account.
- Under Security info click UPDATE INFO >
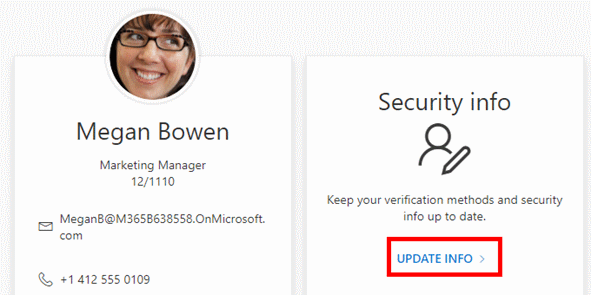
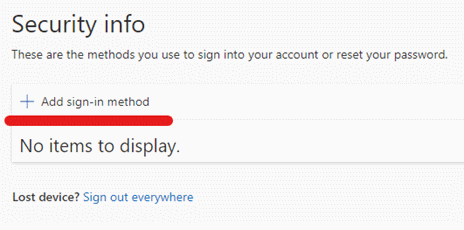
- Click Add sign-in method
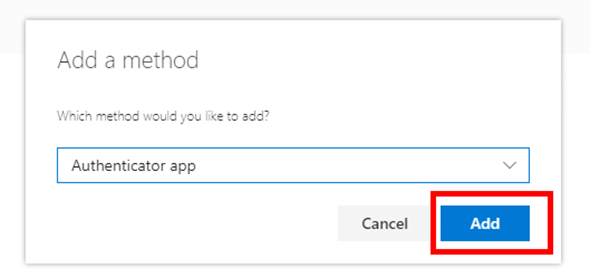
- Select “Authenticator app”, then click Add.
- In your phone’s app store, search for and install “Microsoft Authenticator”.
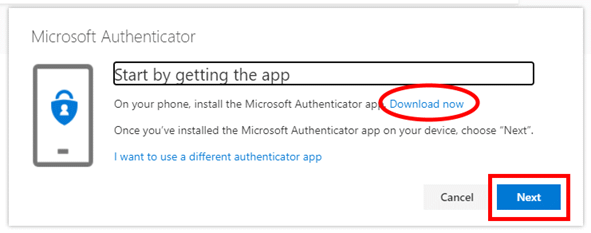
- Click Next, then Next again.
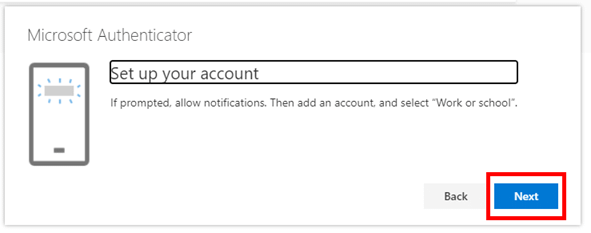
- On your phone…
Open the Authenticator app.
?? If you have not used Authenticator before, you might first be prompted to sign into a personal Microsoft account to facilitate backing up your Authenticator codes. If you have a personal Microsoft account, we recommend doing this. If not, you can create one or skip this process.
- In the menu, click Add account.
- Choose “Work or school account”.
- Tap Scan a QR code.
- Use your camera to scan the QR code presented on your computer screen.
?? Your phone may ask you to give Authenticator permission to use your camera. You need to allow this.
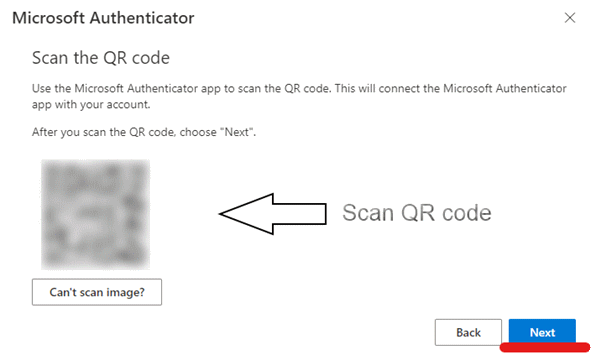
- On your computer, click Next. Note the two-digit number presented on the computer screen. In this case, 28.
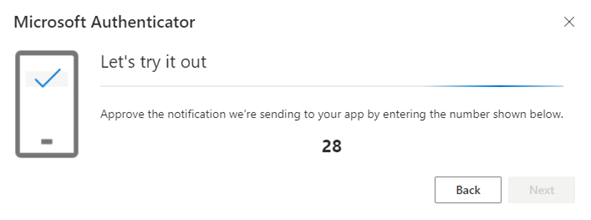
- Back on your phone, the request will pop-up either on your phone screen or as a notification.
- Tap on the notification if necessary, then enter the two digit number, then tap YES (or the tick button) to approve the login.
- Your computer will now automatically confirm the approval. Click Next.
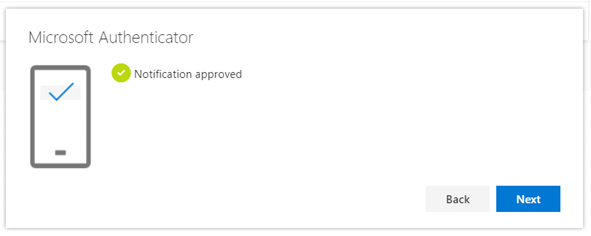
- Setup is complete.
In future when you sign into a new device, or periodically thereafter you may be asked to approve a sign in request on your phone after having entered your password.
?? If you ever receive a sign in approval on your phone when you are NOT signing in, report the incident to your administrator or support team.
01 March 2023
Understanding your Microsoft 365 email quarantine
The Microsoft 365 “email quarantine” captures incoming spam, phishing, malware and other unwanted email in a secure container. Such emails are locked in the quarantine either until they expire, or you request they be released.
Learn more about malicious emails, phishing, and what to do about them.
We are in the process of reconfiguring the quarantine to capture more regular threats for our iBizify-managed Microsoft 365 clients. We are also working to prevent the delivery of certain file attachment types (such as HTML) that are regularly used to carry phishing attacks.
The side effect of this is that on occasion you may find that some benign email that you did want to receive may not reach your Inbox or even your “Junk mail” folder. To counter this, where there is doubt of the legitimacy of one or more email items, you will receive an email from quarantine@messaging.microsoft.com that look like this:
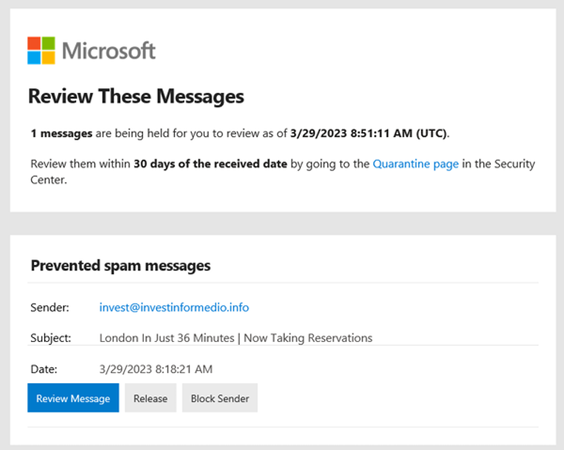
The irony isn’t lost on us, that this important message does look like a phishing email. Check that it is indeed from quarantine@messaging.microsoft.com before you click!
In this notice, you can see who sent the quarantined message, when it was sent, and what the subject is.
You have four ways to respond:
1. Ignore it. The quarantined email will be deleted after thirty days.
2. Review Message. If you aren’t sure about it, you can look at the message safely by previewing its contents.
3. The message will be released to your mailbox.
4. Block Sender. In this scope, this option won't actually have any affect because the sender is already blocked from reaching your inbox.
27 March 2022
Development and integration hours - simplified
We've simplified our pricing structure for development and consultancy services.
Previously only usable for technical support, service packs can now also be used for software / web development, integrations, migrations, and more.
We simply apply a 1.5 multiplier. For example: 2 hours of development would use 3 units; 5 hours would use 7.5 units.
This means it’s now really easy to purchase one or two ten-packs and use them for a variety of projects and support all through one simple billing process.
11 September 2021
We have a new logo
Out with the old and on with the new...

This iBizify is simpler, bolder and more rounded than the old one.
21 July 2021
We have moved
We completed our move to Claydon House in Aylesbury recently - a new workspace to increase productivity, create a professional meeting environment, a bit more desk space, and room to grow. We are very pleased with the results.
Conveniently, our office address now matches what has always been our postal address. You can find our location on Google of course.
Blog
- Webinar: How hackers steal your passwords in 2025 and how to stop them
- Sophisticated new phishing attacks
- Don’t get phished!
- How to set up Microsoft Authenticator
- Understanding your Microsoft 365 email quarantine
- Development and integration hours - simplified
- We have a new logo
- We have moved
- What to look for in a PC for your small business
- Why you should get to know Microsoft Teams
- Making a splash with Acorn Commercials
- Steve raised over £685 for Marie Curie
